EuroPay, MasterCard and Visa (EMV) is a technical standard developed to ensure more secure Point-Of-Sale (POS) transactions. EMV allows non-static information to be transferred between the card, the terminal, and the financial institution that processes credit card transactions. This takes care of skimming fraud where fake devices would copy data from magnetic stripes and use it on another card. While EMV is not new technology and has been in use for over a decade, it has made its way to the US in the last 2 years.
EuroPay, MasterCard and Visa (EMV) is a technical standard developed to ensure more secure Point-Of-Sale (POS) transactions. EMV allows non-static information to be transferred between the card, the terminal, and the financial institution that processes credit card transactions. This takes care of skimming fraud where fake devices would copy data from magnetic stripes and use it on another card. While EMV is not new technology and has been in use for over a decade, it has made its way to the US in the last 2 years.
How does EMV Technology work?
EMV uses microprocessor chips that encrypt bank information making it far more secure than the old magnetic stripe cards. Magnetic Stripe uses static data that is stored in the stripe on the card (this makes it unsafe considering it can be stolen and used). The static information means that the number transmitted by the card for all transactions is the same.
 When it comes to EMV standard, although the card data will be the same for every transaction, there will also be other pieces of data that gets re-organised for every transaction. This renders the data stolen at the POS useless for further use.
When it comes to EMV standard, although the card data will be the same for every transaction, there will also be other pieces of data that gets re-organised for every transaction. This renders the data stolen at the POS useless for further use.
The verification method for EMV cards can be chip-and-pin or chip-and-signature, with the former being the preferred choice in Europe and the latter often used in the US. This is contactless transaction which is becoming popular as NFC (Near Field Communication) technology used by mobile payments is making inroads. While technological advancements are racing ahead to reduce frauds, fraudsters are not far behind, as they continue to seek innovative methods.
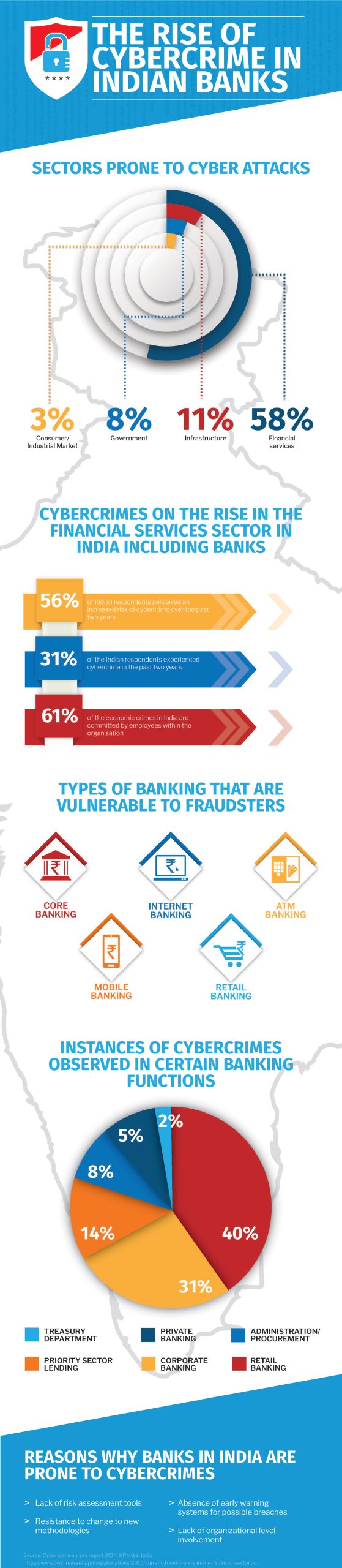
Fraud, the scare still exists
While POS frauds and card counterfeiting have reduced in countries that are early EMV adopters, the cybercrime scene has now shifted to the canvas of e-commerce and online transactions. Fraudsters are also keenly watching late EMV adopters as potential targets. With data breaches and online theft increasing, security agencies have reported a doubling in crime rates of online frauds. ATM frauds are not far behind – swindling with counterfeiting cards and duping to snatch PIN numbers are on the rise.
Research analysts report that these types of frauds are more damaging to the customer by the day. The frauds go unnoticed as the unauthorised purchases and withdrawals lie hidden in the transactional details list. Not many customers go through their transaction histories regularly and closely.
The microchip comes into play when trying to prevent counterfeit fraud because it makes it harder to produce a copy of the card. And a PIN comes into play for protecting against lost-or-stolen fraud because it makes it impossible to use the card unless they also know the PIN.
EMV adoption and the changing fraud types
 Using EMV technology for cards has seen a reduction in skimming-type attacks, but the crime rate has increased in other ways of stealing money. Research firm Aite Group reports that losses from counterfeit, lost, and stolen cards in Canada dropped from $245 million in 2008 to $112 million in 2013.
Using EMV technology for cards has seen a reduction in skimming-type attacks, but the crime rate has increased in other ways of stealing money. Research firm Aite Group reports that losses from counterfeit, lost, and stolen cards in Canada dropped from $245 million in 2008 to $112 million in 2013.
A research by the European ATM Security Team (EAST) found that fraud-type attacks increased 28% during the first half of 2016 with cyber criminals stealing €174 million and Aite reported that there was a 79% increase in online fraud during the EMV adoption phase in Europe.
The banking sector is now making a move to bring in EMV-chip-enabled credit and debit cards, which generate a unique transaction code with each purchase, making them harder to spoof. With these systems and cards rolling out, mining credit card numbers will not be as valuable for criminals, says Privacy Rights Clearinghouse.
Precautionary steps
While fraud severely erodes customer confidence and the bank’s bottom line, fraudsters continue to keep pace with the very technologies that are being developed to keep them at bay.
While banks conduct frequent security audits, invest in advanced security measures and work proactively in mitigating risks, there’s no silver bullet that can eliminate fraud completely.
However, it does help to have an intelligent, pro-active, well-synchronised cross-channel system in place that –
- Understands customers’ transaction patterns at a granular level using information from across all channels
- keeps track of customers’ credit histories
- screens transactions in real-time to quickly spot unusual / potentially suspect activity
- applies login authentication rules (including mobile number / email id updates)
- activates real-time alerts and notifications while potentially suspect transactions are in progress
To effectively combat fraud, Banks must go beyond conventional anti-fraud solutions. Intelligent platforms are now available that harness data in real-time from across channels to not only deliver a unified anti-fraud mechanism but also helps create a secure ecosystem.