In the Middle East’s rapidly evolving financial ecosystem, where innovation, cross-border remittances, and international trade converge, a persistent threat undermines progress: money mule fraud. Criminal networks recruit individuals—sometimes knowingly, often unknowingly—to transfer illicit funds through personal accounts. Exploiting the region’s growth as a global financial hub, particularly in the UAE, Saudi Arabia, Qatar, and Bahrain, these schemes channel billions in unlawful proceeds each year, eroding trust in financial institutions.
Why Mule Fraud Is Surging in the Region
Digital Channels, Rising Exposure
The shift to digital banking has expanded customer reach but also widened the attack surface for phishing, malware, and social engineering tactics used to recruit money mules.
Vulnerable Expat Communities
In the Middle East , GCC nations host large expatriate populations. Financial pressures make some individuals susceptible to fraudulent job offers or “remote roles,” turning them into unwitting accomplices.
Cross-Border Account Sourcing
Mule networks tap accounts in South Asia and Africa. Recent investigations in India exposed mule recruiter rings tied to Dubai-linked syndicates, highlighting how regional flows remain deeply entangled with GCC markets.
Remittance Volumes as a Smokescreen
The region’s large remittance corridors provide cover for illicit flows, allowing fraudsters to mask suspicious activity within normal transactional traffic.
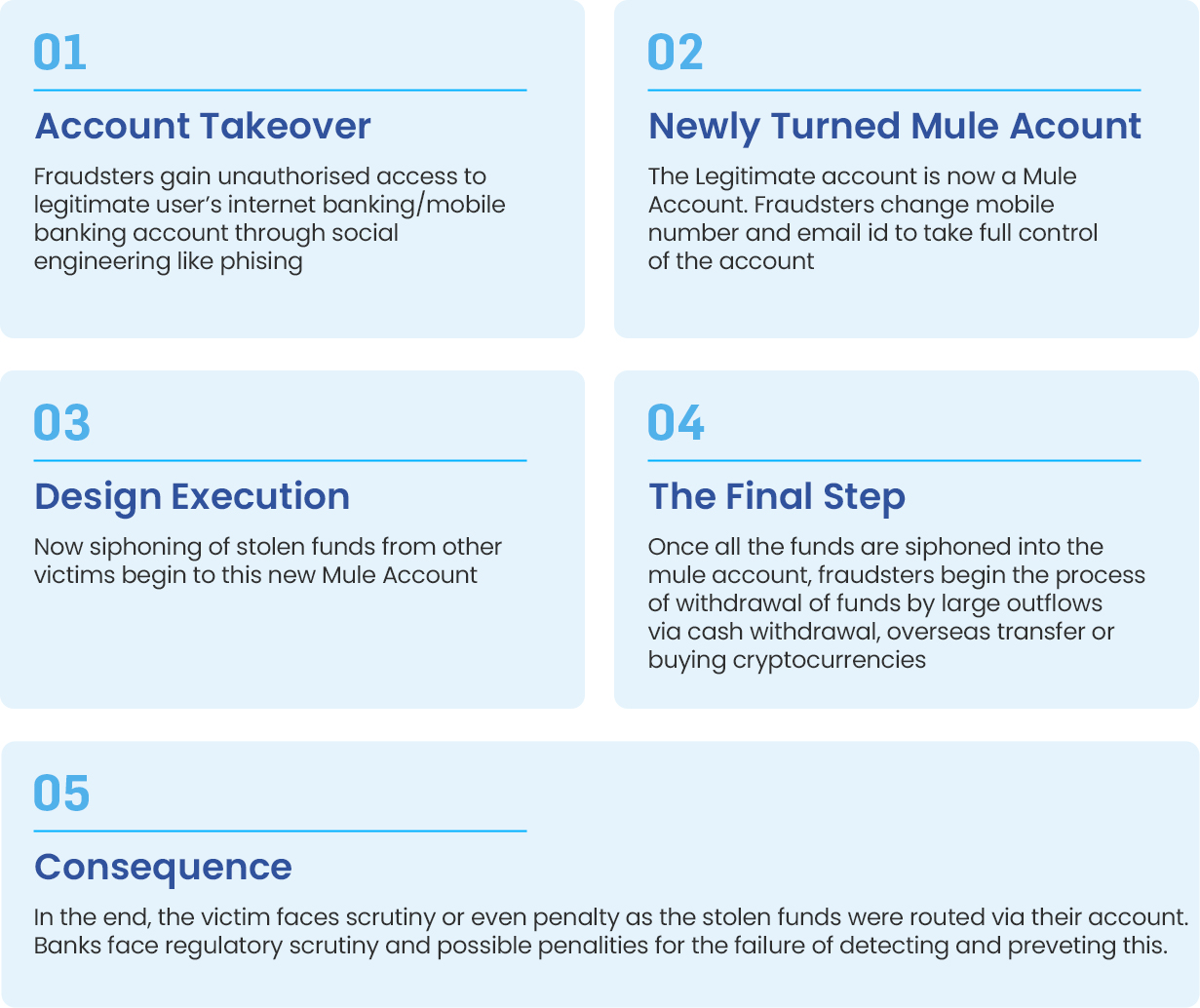
Modus Operandi of Money Mule Frauds
Money mules fall into two broad categories: knowing (witting) and unknowing (unwitting) participants.
Knowing mules actively collaborate with criminals for profit, while unknowing mules are deceived through scams like fake job postings, romance frauds, or promises of easy money for tasks like receiving and forwarding funds. In the Middle East, these typologies are amplified by the region’s expatriate workforce and digital nomad culture, where economic vulnerabilities in countries like India, Pakistan, and the Philippines feed recruitment pipelines.
Mule operations function through sophisticated rings—organized, hierarchical networks resembling illicit businesses. These rings recruit en masse via social media, dark web forums, or encrypted apps like Telegram and WhatsApp, targeting vulnerable groups such as students, retirees, or unemployed expats. Once recruited, mules receive illicit funds into their accounts, which are quickly disbursed to other mules or endpoints, creating a layered “smurfing” effect to obscure the money trail. In the GCC, Dubai and Riyadh serve as coordination hubs, with rings leveraging cross-border ties to South Asia and Africa for account sourcing.
For example, syndicates linked to UAE-based operations have been dismantled in India, revealing how funds from cybercrimes like phishing or ransomware are funneled through expatriate accounts before exiting to offshore havens. These rings use compartmentalization—recruits rarely know the full network—to minimize risks, and they evolve rapidly, incorporating AI-driven recruitment bots and encrypted communication to scale operations globally.
Mule Modus Operandi via Social Engineering Scam
Authorized Push Payment (APP) scams (a common vector for mule involvement) in the Middle East specially in UAE are projected to cause losses exceeding $30 million by 2028, fueled by real-time transaction fraud and social engineering.
Mule fraud is increasingly multidimensional: mixing technical evasion, physical & human logistic components, trust-building deception.Defense must also be multidimensional: no single countermeasure suffices. Detection needs to be continuous over the lifespan of an account.Emerging tech (GPS spoofing, device hand-over, physical shipment of devices) raises the bar for fraud detection as fraudsters are innovating around previous blockers.
Evolving Expectations from Regulators and Banks
Stronger Onboarding & Monitoring Controls
Regulators across MENA are intensifying efforts to combat financial fraud, focusing on real-time fraud monitoring, mule detection, and device intelligence. Countries including the UAE, Saudi Arabia, Qatar, Bahrain, Kuwait, and Oman have issued regulations mandating advanced fraud prevention tools. Non-compliance results in hefty fines, as seen in recent enforcement actions.
| Regulatory Body |
Regulatory Requirement |
| Central Bank of UAE (CBUAE) |
On 23 May 2025, the UAE Central Bank (CBUAE) issued Notice No. CBUAE/FCMCP/2025/3057, mandating stronger authentication for digital banking and e-wallet transactions—banning SMS/email OTPs and static passwords, and requiring biometrics or secure in-app verification—to curb account takeovers and mule recruitment. The notice also strengthens fraud prevention by ensuring consumers verify payee details before fund transfers, helping banks detect and block mule-related transactions, with liability on banks for fraud in improperly authenticated transfers. |
| Saudi Arabian Monetary Authority (SAMA) |
Circular No: 000044021528: SAMA’s preventive control requirements mandate strong customer authentication, transaction monitoring, device intelligence, and restrictions on risky behaviours (e.g., VPN use, multiple logins, unusual transactions) to stop account compromise and mule activity. Specific measures like blacklisting, mule account identification, dormancy monitoring, and payee/transaction verification aim to block fraudulent fund flows and disrupt mule networks. |
| Qatar Central Bank (QCB) |
Issued in September 2024, QCB specifically emphasised that AI is expected to be used by licensed financial institutes for fraud detection and prevention, mandating robust risk management. |
| Central Bank of Bahrain (CBB) |
The Central Bank of Bahrain (CBB) mandates licensed financial institutions to implement transaction monitoring systems, including automated systems for larger institutions for fraud prevention efforts outlined in the CBB Rulebook. Institutions must use risk-based monitoring tailored to their business complexity and customer base, and employ stringent customer due diligence processes to identify suspicious activities and potential mule fraud. |
| Central Bank of Kuwait (CBK) |
The Central Bank of Kuwait (CBK) strengthens fraud prevention through electronic payment regulations, cybersecurity frameworks, and customer alerts that emphasize using strong passwords, secure PINs, and official channels to block scams and mule activity. At the same time, CBK promotes innovation via its fintech sandbox “Wolooj” and GCC-level initiatives, encouraging the adoption of AI and advanced technologies in banking. |
| Central Bank of Oman (CBO) |
On 25 September 2023, the Central Bank of Oman (CBO) issued a Cybersecurity Framework Circular requiring banks, finance companies, PSPs, and exchange houses to strengthen governance, technology, and online service controls—covering device risks, suspicious transaction monitoring, and fraud prevention mechanisms relevant to mule detection. Further, under Decision No. 25/2025 (effective 1 June 2025), CBO introduced the Regulatory Framework for Digital Banks, mandating robust digital onboarding, AI-driven risk management, and consumer protection measures to counter evolving fraud and financial crime threats. |
Real-Time Detection and Intelligence Sharing
Institutions across the Middle East are adopting real-time systems to flag patterns like burst transactions, multiple rapid payees, or sudden reactivation of dormant accounts.
Real-time inbound transaction monitoring
is critical, scrutinizing incoming payments to identify mule activity at its entry point. Unlike outbound monitoring, inbound analysis examines the source of funds, velocity of receipts (e.g., multiple high-value transfers from unrelated accounts), and contextual signals like unusual sender patterns or geographic mismatches.
For example, a dormant account receiving large inbound wires from high-risk jurisdictions could indicate mule initialization. Machine learning models profile these inflows in milliseconds, integrating device fingerprints, IP geolocation, and behavioral biometrics to distinguish legitimate remittances from fraud. This proactive layer prevents mules from disbursing funds onward, reducing losses by up to 70% in early pilots. Alert thresholds include rapid inbound bursts exceeding account norms, mismatched beneficiary details, or links to known scam vectors, with automated holds triggered for investigator review.
What This Means for CXOs in Banks
Mule fraud is not a compliance checkbox—it’s a systemic, reputational, and financial risk requiring enterprise-wide attention. Banks must:
- Stop mules at the stage of onboarding
- Fuse device, behavioral, transaction, and external threat intelligence
- Deploy integrated, real-time detection across digital and payment channels
- Leverage consortium models for shared visibility into mule activity
- Educate customers proactively, especially in markets like Oman, where awareness remains nascent
Clari5’s Approach: Intelligence-Led, Multi-Layered Defense
Clari5 combats mule fraud with real-time, intelligence-driven capabilities tailored to regional risks, ensuring robust protection for banks. Designed for high scalability, Clari5’s platform handles peak transaction volumes, processing up to 10,000 transactions per second (TPS) to meet the demands of large GCC financial institutions. The system ensures low latency and high throughput, even during high-traffic periods like Ramadan or major e-commerce sales events, maintaining robust performance without compromising detection accuracy. Scalability is achieved through a distributed, cloud-native architecture, seamlessly handling millions of daily transactions while integrating with existing banking systems.
Mule accounts can emerge at any point in the customer journey—during onboarding, while processing live transactions, or even within dormant portfolios. To counter this evolving threat, Clari5 applies a layered defense strategy, combining device intelligence, AI, behavioral analytics, and regulatory-aligned scenarios. This ensures banks can detect and disrupt mule activity early, prevent misuse during high-risk transactions, and continuously monitor portfolios for hidden risks.
Mule Fraud Prevention at Onboarding
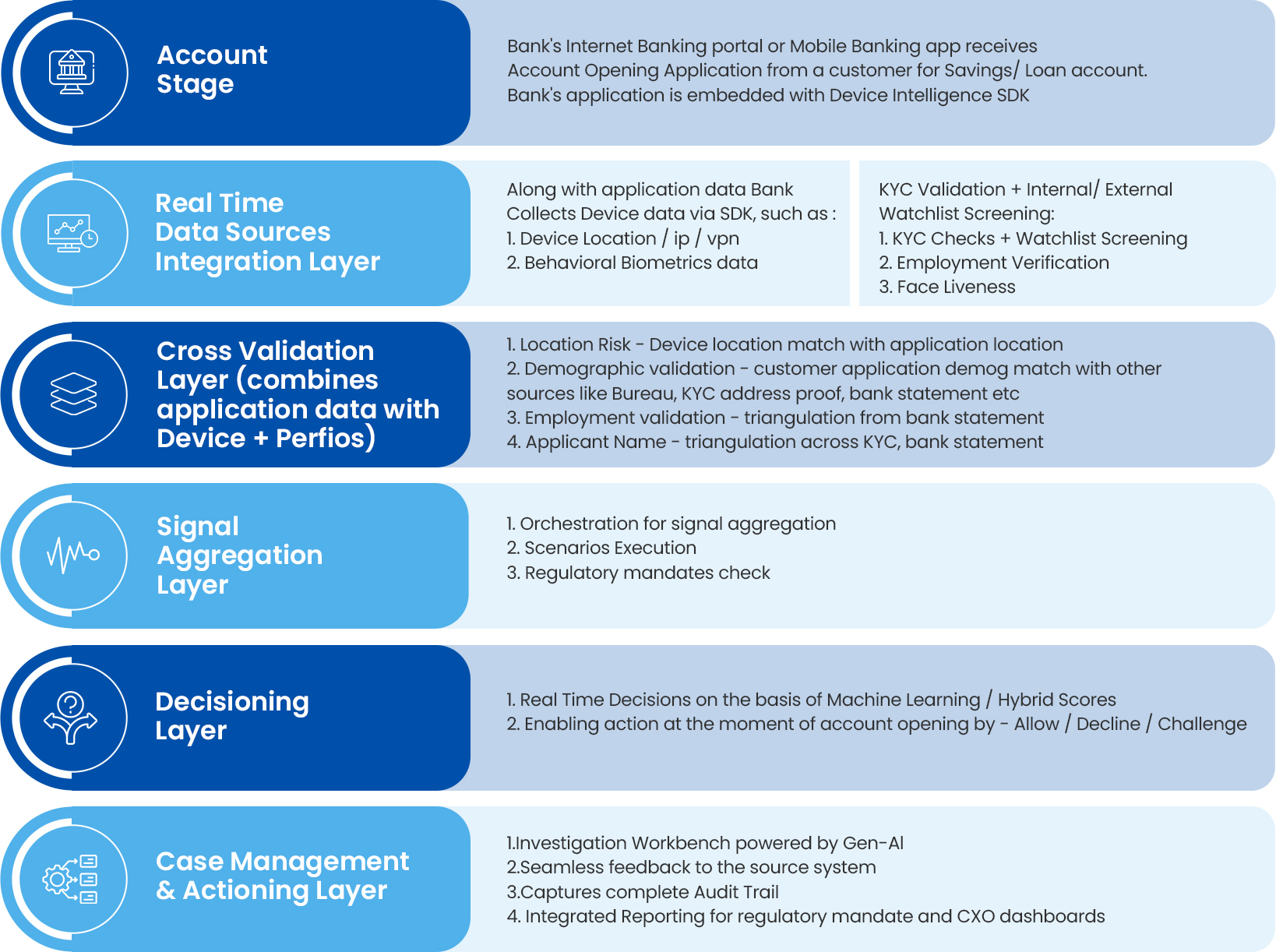
Mule Fraud Detection Points at Onboarding
Robust identity verification and device intelligence form the core of strategies to combat fraudulent accounts in onboarding processes. Identity checks include ID validation through cross-referencing with records, biometric recognition with liveness detection to counter deepfakes and spoofing, deduplication to prevent identity reuse, and AI spoof detection for altered images. These help thwart fraudsters using stolen or fake IDs for multiple accounts. Device and network intelligence involves fingerprinting hardware and software to spot device reuse, behavioral biometrics like keystroke and mouse patterns to identify bots or impersonators, monitoring IP, VPN, TOR, and GPS for suspicious locations or impossible travel, and analyzing network velocity for cartel-like patterns. Document and employment verification entails checking authenticity of uploaded files like salary certificates through metadata and issuer consistency, verifying employers via application velocity, digital photos/videos of premises, and cross-validating details against external data sources and bank statements to expose fake setups.
Behavioral and velocity controls monitor multiple applications from the same individual, company, or IP, detect policy gaming through manipulated parameters, and block retries using identical IDs, numbers, or emails to limit fraudulent attempts. Risk intelligence includes historical analysis across products like cards and loans, detecting syndicated fraud via correlated data, real-time risk scoring, and automated flagging for investigation.
Additional measures encompass geolocation risk checks for high-risk areas or proxies, managing whitelists/blacklists for known fraudulent entities, and integrated alerts for escalation. Overall, integrating these real-time checks—spanning device intelligence, identity verification, document validation, and velocity monitoring—prevents fraudsters from onboarding before any exposure occurs.
Mule Fraud Prevention During Transactions
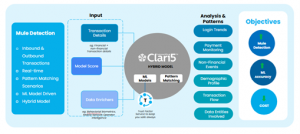
Clari5 fuses advanced pattern recognition, machine learning models, and hybrid scorecards to stop mule transactions in-flight, providing real-time alerts and automated intervention:
- Dormant Accounts Suddenly Active: Spikes in inflows/outflows trigger alerts. The system cross-checks historical account activity to detect atypical usage patterns and flags accounts dormant for weeks/months that suddenly show high-value movements.
- High-Value Credits with Rapid Drainage: Identifies mule accounts used for quick laundering by tracking funds that are credited and almost immediately withdrawn or transferred. Clari5 also correlates this with counterparties’ risk profiles to prevent repeat laundering attempts.
- Suspicious New Accounts: Early detection if high-value activity occurs within 48 hours of account opening. The engine considers device fingerprints, geolocation anomalies, and previous blacklisted identifiers to block potential mule onboarding at the transaction stage.
- Post-Mobile Number Change Activity: Detects surges often tied to mule takeovers. Any significant deviation in transaction behavior post-KYC updates (phone/email changes) is scored and monitored for rapid intervention.
- Small Credits, Big Debits (Structuring): Monitors structured transaction patterns commonly linked to mule rings. This includes multiple small deposits followed by a large single withdrawal, signaling layering or distribution attempts.
- High-Velocity Digital Transactions: Flags abnormal frequency across multiple devices, IPs, or geolocations relative to the declared customer profile. Cross-channel behavior is analyzed, including mobile, web, and API-based transactions, for consistent risk scoring.
- Machine Learning Score (0–1000 Scale): Aggregates financial, behavioral, and non-financial signals, including geolocation anomalies, device fingerprinting, login behavior, transaction velocity, and relationship networks. Scores are dynamically updated in real-time to reflect emerging risk.
- Hybrid Scorecards: Merge machine learning predictions with pre-defined scenario insights to minimize false positives while ensuring swift action. Automated holds, alerts, or blocks are triggered based on risk thresholds, and cases are routed for further investigation if needed.
- Cross-Account and Network Analysis: Detects potential mule rings by linking transactions across multiple accounts, even in different entities, using network analytics to reveal hidden connections and coordinated fraud attempts.
- Adaptive Risk Profiling: Continuously updates customer risk profiles using historical behavior, device intelligence, transaction patterns, and external threat intelligence feeds. This ensures that risk scoring evolves with changing fraud tactics.
- Regulatory & Audit Alignment: Maintains a fully auditable trail of flagged transactions, actions taken, and model decisions, supporting compliance with local regulators such as CBUAE , SAMA etc.
Case Study: Mule Fraud Detection at Scale
A large universal bank in Asia , managing over 150+ million accounts, faced a persistent challenge of mule fraud.
On average, the bank was detecting only 3 mule accounts per day, leaving the institution exposed to
large-scale fraud risks.
To address this, the bank deployed the Clari5 platform, which leveraged a hybrid model of scenarios and machine learning. By analyzing transactions (incoming, outgoing, balances) alongside customer data, the system was able to uncover hidden mule patterns that traditional methods had missed.
Results after 3 months:
- Mule account detection surged from just 3+ per day to over 250+ per day.
- The bank now had far greater visibility and control over mule activities, significantly strengthening its fraud defense posture.
This transformation underscores the impact of advanced fraud detection platforms like Clari5 in proactively combating mule fraud at massive scale.
Conclusion
Money mule fraud silently erodes the region’s financial integrity, and syndicates are becoming smarter, faster, and harder to stop. For GCC bankers and regulators, the mandate is clear: adopt real-time, intelligence-driven systems that can learn, anticipate, and block mule networks before they escalate.
With Clari5, financial institutions across the Middle East can:
- Stay ahead of regulatory mandates
- Safeguard revenue and brand reputation
- Protect customers from unknowingly becoming part of criminal networks
Now is the time to act—partner with Clari5 to turn mule fraud from an invisible threat into a visible,
preventable risk.